HackTheBox - HDC
Hack The Box is a great platform for hackers/penetration testers to practice and learn with. Their site has a plethora of hacking content including challenges specific to a category of your choosing. This allows you to hone your skills in that specific area to take into the labs or wherever you please. “HDC” is a Web Application hacking challenge and will be the focus of this writeup.
HDC overall was pretty easy, I’ve followed the bug bounty world for a while now and have practiced bug bounty a bit myself. I’m decent at reading web-based source code and that came into play with this challenge.
Initial Enumeration
I know this is a Web Challenge, and Web Challenges are geared toward honing your web application hacking skills. Since this isn’t a typical machine on the Hack The Box, I skip the normal nmap scan and go straight for Gobuster while I look around on the site.
gobuster dir -u http://docker.hackthebox.eu:31791/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 50
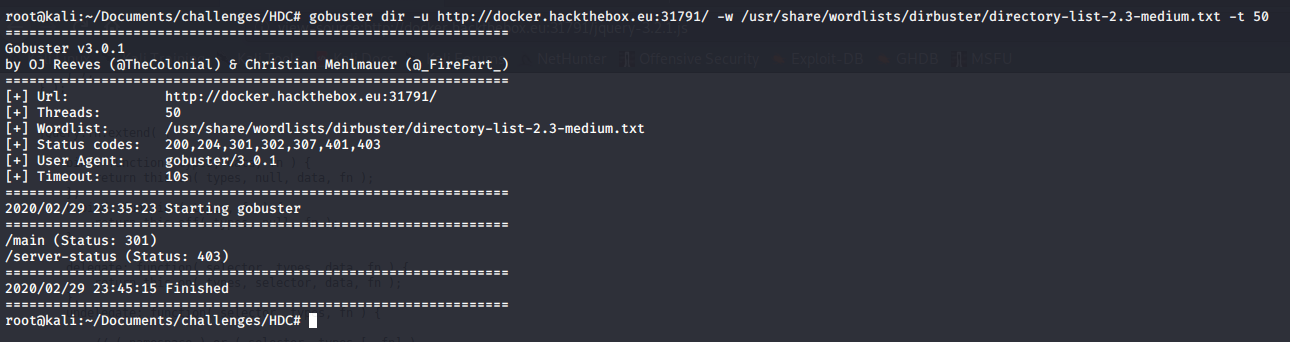
Gobuster comes up with nothing useful, just some default pages. I haven’t been wasting time however, I’ve been digging into the source code of the login page.
Web Page Enumeration
Here is the login page for HDC:
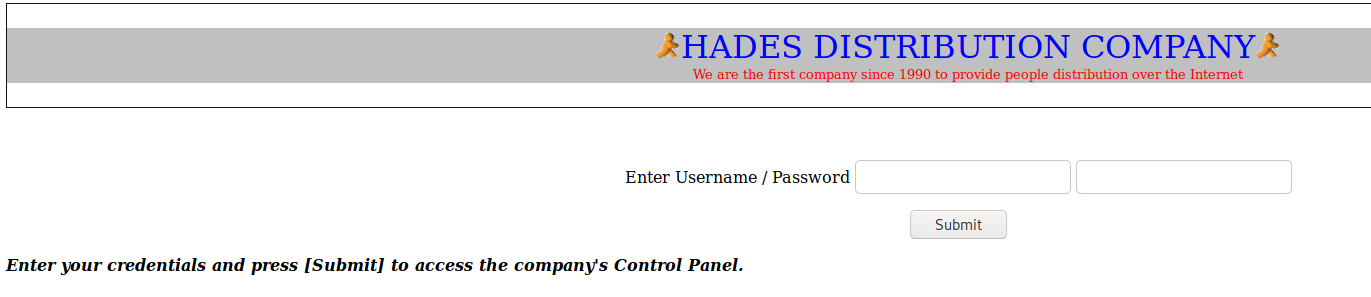
I threw some SQL injection and username:password credentials into the input fields, but got no leads. Looking into the source code, I can see two .js files:
jquery-3.2.1.js
myscripts.js:
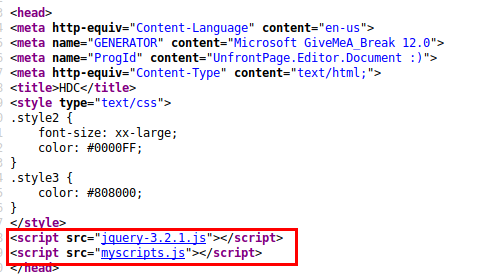
jquery-3.2.1.js was huge, but myscripts.js shows a simple doProcess() function that seemed to be useful. It seems like it was a submission command linked to “formaki”:
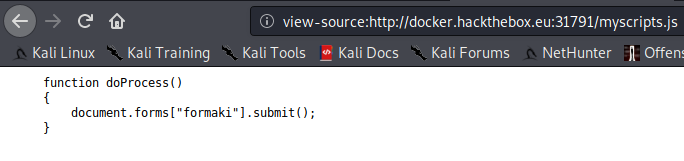
I remember seeing “formaki” in the login page source code, and this seems to be a submit function, so I use Inspect Element on the username and password input fields. Here I find two text inputs:
name1
name2
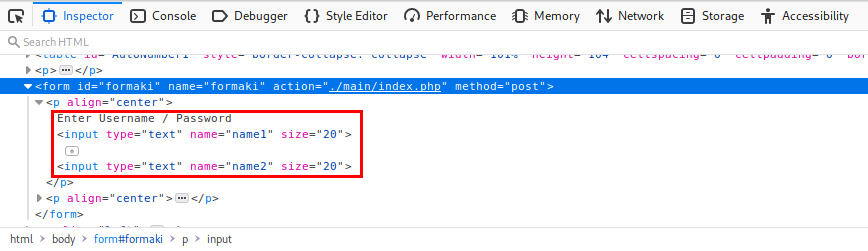
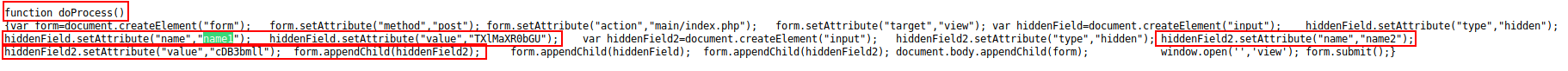
Going back to the large jquery file, I do a search for name1 and name2 and find some hidden fields containing the credentials needed to authenticate:
Once logged in, I look around a bit and immediately see a lead to enumerate email addresses. This is the objective of the challenge, to send an email to “the certain individual who uses this website for shady business”. Once I access the “Mailbox of Special Customers” page, I use Inspect Element again and discover a /secret_area_/ path linked in the HTML:
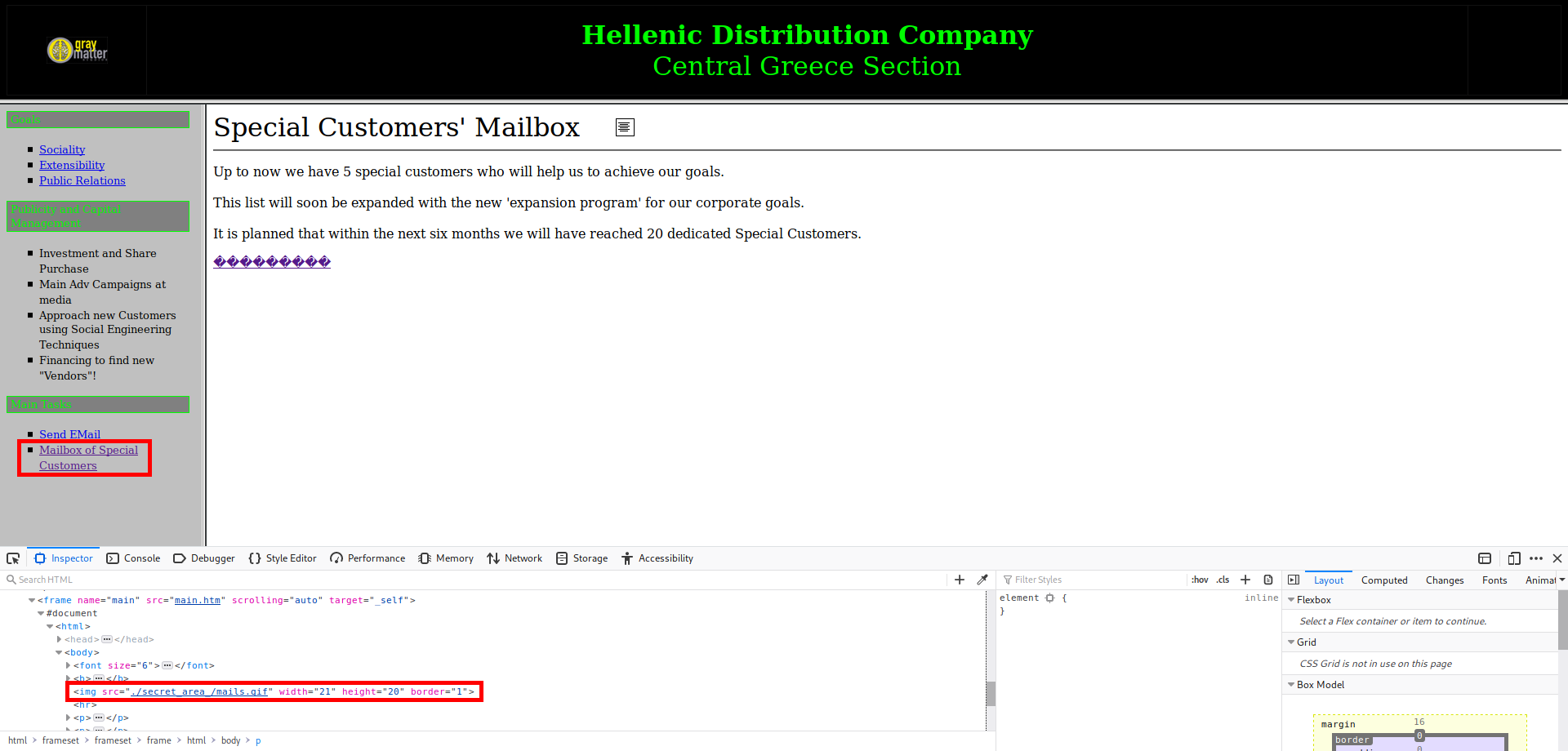
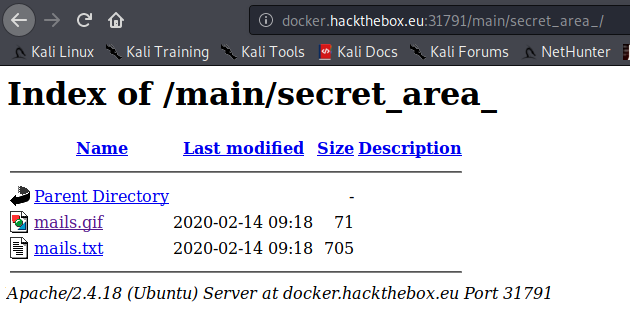
After accessing /main/secret_area_/, there is a mails.txt file:
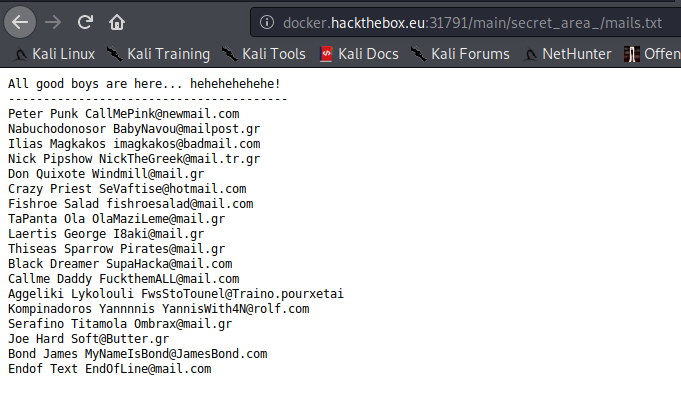
Inside the mails.txt file, there is a promising list of email addresses that could be used to get the flag:
Exploitation
I take note of the email addresses and go to the “Send EMail” page I noticed on the home page, linked right above “Mailbox for Special Customers”:
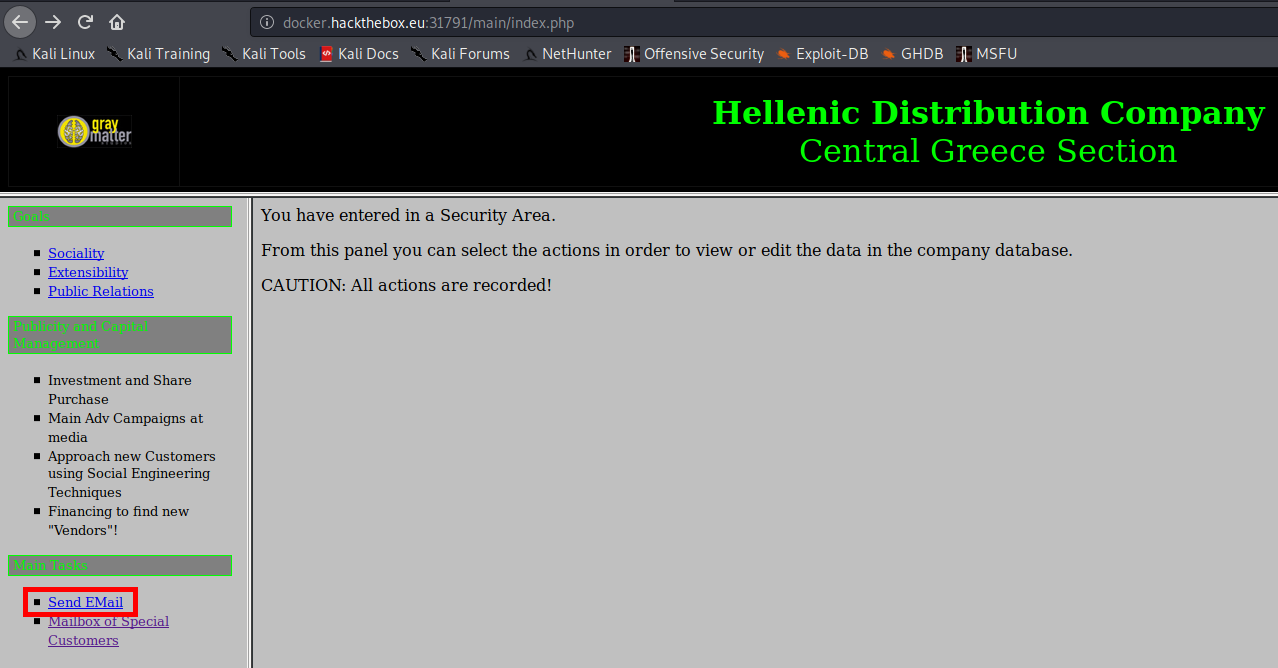
The link leads to a control panel that allows you to send email:
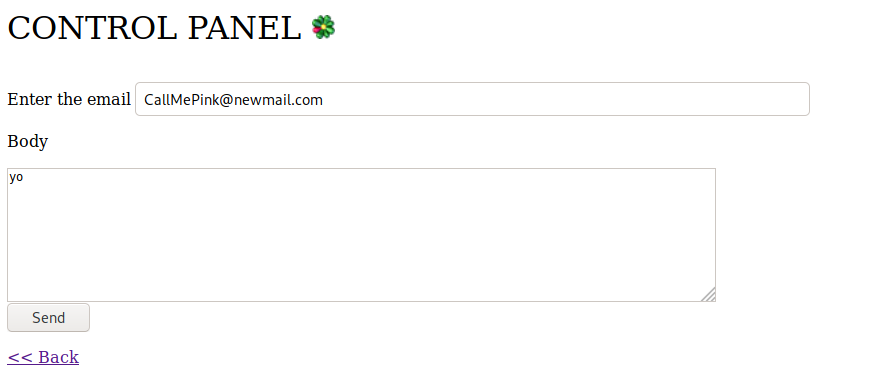
Immediately I open the Burp Suite proxy and intercept the send email request:
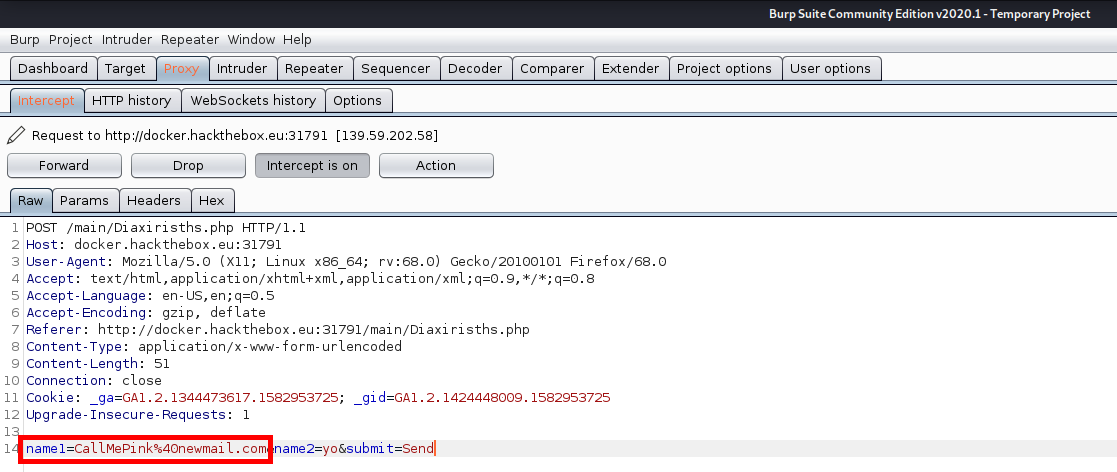
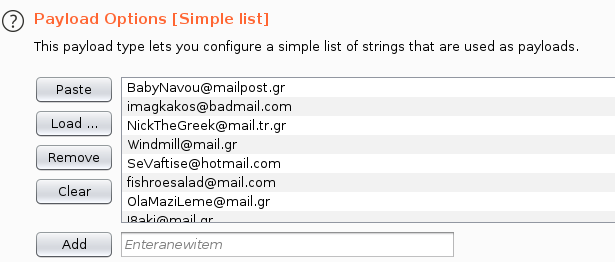
From here I can put the request into Burp Suite’s Intruder, configure the payload, and easily send email to all of the email addresses in the payload:
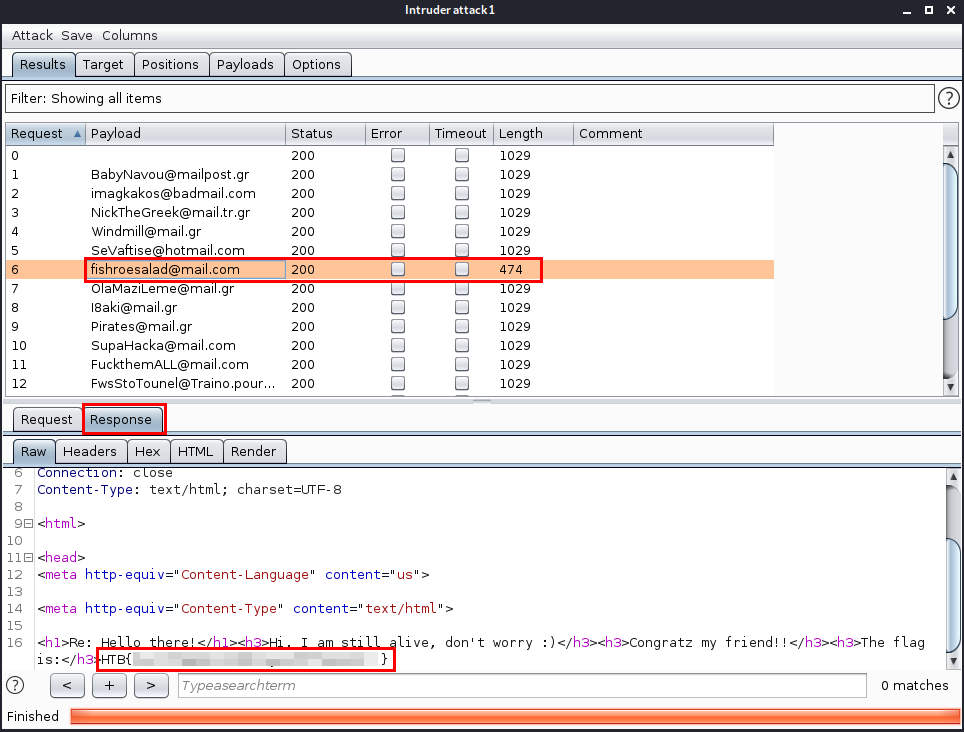
I start the attack, and find the flag in the response from “fishroesalad@mail.com”:
Conclusion
HDC was pretty simple, but a great way to get back into CTFs. I’ve been gone for a while, busy in life with job promotions but still around and learning. My goals are the same and I continue to pursue them. You can find me in the Hack The Box Discord server, or contact me on Twitter @rootcollector.