Path to OSCP - Week 2 - Domain Admin
PWK Labs - Week 2
This week I managed to compromise one of the Active Directory domains in the new PWK labs
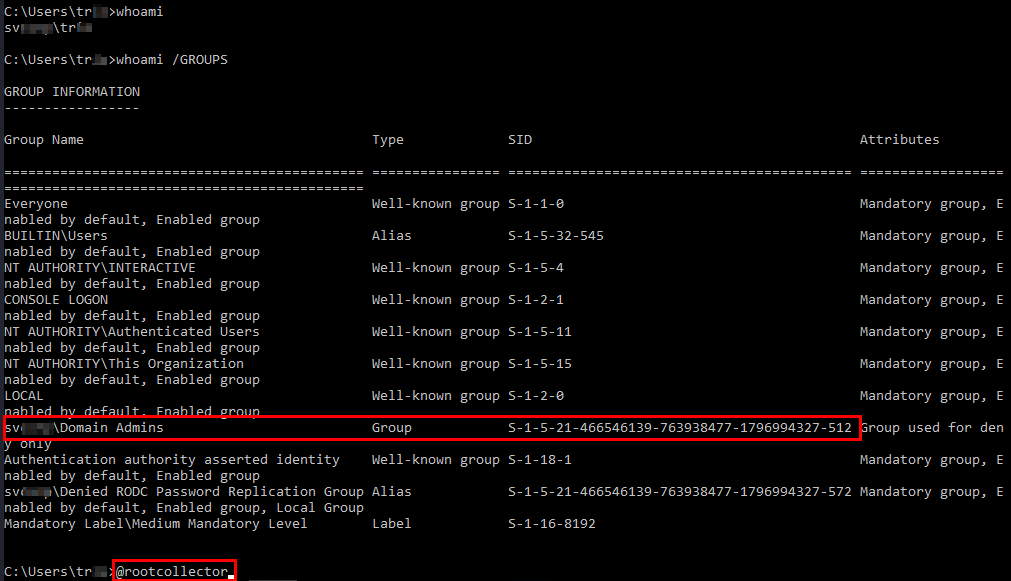
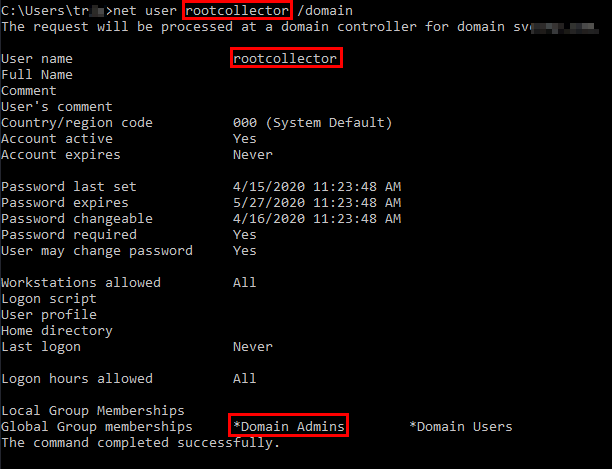
I’d performed some Active Directory penetration testing through Hack The Box in the past but this was on another level and was very fun, props go to Offensive Security for this new addition to their PWK labs. I started off as a low privileged user, pivoted and compromised multiple machines and users on the domain, then took control of the domain controller. My professional IT experience came into play as I’ve been studying the inherent flaws of Windows, Kerberos, Active Directory, etc. for a while while working professionally and seeing what is normal in a domain. I’ve been waiting for the chance to test my skills on a lab domain rather than a singular machine on Hack The Box.
I also compromised some of the normal lab machines and learned a great deal from them. I’m amazed at how the machines seem to be built to teach you a specific lesson and that makes me glad that I decided to attack the labs sooner rather than later. I’ve compromised 18 machines so far out of 75, up from 8 last week.
Takeaways
Be More Thorough
As I said, it really seems the PWK lab machines are designed to teach you a specific lesson. I’ve learned to be more thorough with my enumeration and not always attack the most attractive port with the highest attack surface. For me, it’s become a habit to rule out other common ports (FTP, SSH, 139/445, etc.) or take them to their limits before attacking 80/443. Also, sometimes the initial nmap scan with service versions will show you the attack vector, so be sure to search for exploits related to those services before diving too much into something.
Practicing Simplicity
Also, I’ve learned to K.I.S.S., Keep It Simple Stupid. I’ve been hacking for a few years now and I find myself making things way too complicated right off the bat. I’ve learned to take a more simple and thorough approach when leveraging certain exploits, and being more patient with enumeration to develop an organized and structured attack. Also, in a particular case on a machine I can’t discuss, I found it’s useful to quickly try an exploit just to rule it out really fast. For example, I found and LFI exploit on Exploit-DB for the version of the web server I was attacking and went deep enumerating the server. Eventually I was able to read the web server config file through a Base-64 request, it turns out the server had RFI enabled the entire time and I could have tested that first before going down the LFI path. This may not be good practice for the real world, but in the PWK labs it doesn’t hurt to at least try.
Utilize the Forums
I hear people all the time say to avoid the forums. I agree to an extent, but if you’re working on a machine for a couple of hours and you can’t seem to get a foothold on it, go to the forums and quit wasting your valuable time. You need to learn before you can practice, rather than taking shots in the dark out of desparity. I’m not going to lie, I’ve used the forums on a few machines but I feel like I have a good disciplined approach to it as I only look for what I’m stuck on and I take extensive notes and research as much as I can on what I didn’t know or understand. This way I turn hours of struggling mindlessly into a learning experience, and I get to better use those hours of struggling to attack more machines in the lab and learn more. If you don’t take good notes on what you didn’t understand, you’re not doing it right.
Conclusion
Another good week of the PWK labs. My objective is to get at least 50-60+ machines under my belt in my lab time, own another Active Directory domain, and get a lot of Buffer Overflow practice in so I can ace that on the exam. Depending on how I feel I may even delay my exam and work on more OSCP-like machines on Hack The Box.